When you receive a URL in https, you are asked to either accept a certificate or the certificate has already been accepted. In the second case, you can still check the server certificate.

There are default certificates known by browsers like:
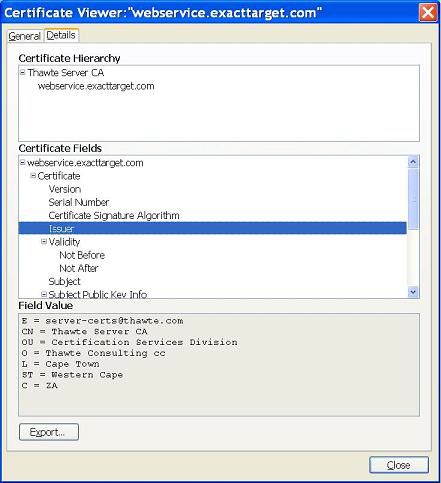
The CA is the authority that validates the server. The certificate to add to the CA list is the authority certificate, not the server certificate. In other words, get the server issuer certificate (and all the parents, grandparents, and so on). For example, if your server is validated by Thawte, add the Thawte certificate to the list.
To check your certificate is the CA one, search for the CNs (Common Names) in the .cer files. The CA Subject entry (below in red) should be the Issuer CN in the server certificate (above screenshots).
openssl x509 -in server.pem -noout -subject
gives:
subject= /C=ZA/ST=Western Cape/L=Cape Town/O=Thawte Consulting cc/OU=Certification Services Division/CN=Thawte Server CA/emailAddress=server-certs@thawte.com
To convert a .cer certificate to the .pem format used by GWS:
openssl x509 -inform DER -in server.cer -outform PEM -out server.crt
Sometimes the CA hierarchy described in the server certificate is incomplete or needs another certificate (default ones use by browsers or private ones).
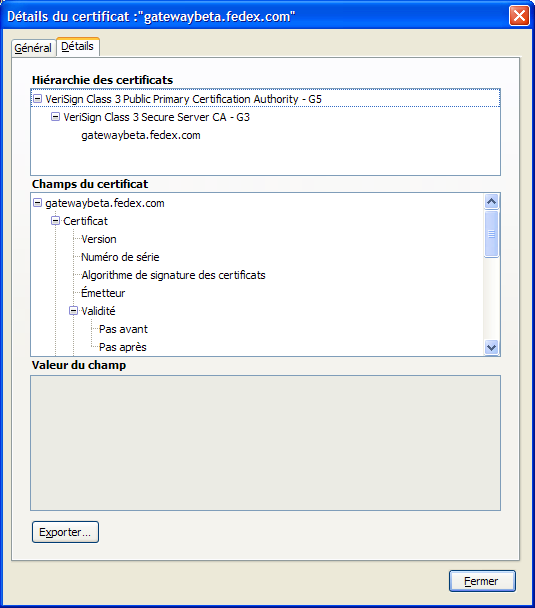
When this occurs, you will have this kind of error message when you set FGLWSDEBUG:
WS-DEBUG (Security error) Error with certificate at depth: 3 issuer = /C=US/O=VeriSign, Inc./OU=Class 3 Public Primary Certification Authority subject = /C=US/O=VeriSign, Inc./OU=Class 3 Public Primary Certification Authority err 19:self signed certificate in certificate chain WS-DEBUG END
This means openssl is looking for a third ancestor that is not listed in the hierarchy above. In this example, gatewaybeta.fedex.com only has two ancestors, and none are named "Class 3 Public Primary Certification Authority". You need to download the root certificates from VeriSign and add "Class 3 Public Primary Certification Authority" in your CA list.