Back to Contents
Authentication in the Genero Application Server provides the ability to:
- Start an application with authenticated user rights using a user's
environment, profiles, access privileges, and so on.
- Provide a Single Sign-On (SSO) solution.
Topics
Authentication for applications served by the Genero Application Server
utilizes the Kerberos protocol. Kerberos is a secure method for authenticating a
request for a service in a computer network.
A free implementation of this protocol is available from the Massachusetts
Institute of Technology (http://web.mit.edu/Kerberos).
Kerberos is available in many commercial products as well.
Active Directory provides central authentication and authorization services
for Windows-based computers. Kerberos is used by default for authentication in
Active Directory.
Back to the top
Implementation constraints are related to the Kerberos architecture and
implementation.
- A well-configured Active Directory / Kerberos server is required.
- Clients (to include the User Agent and Web Server Connector) must have
network access to the Kerberos server.
Windows Only:
- The Web Server (Apache or IIS) must be launched as either the
host account or a domain user account. It must not be launched as a local user account.
- The Genero Application Server must be launched as either as the
Local System Account (the account, by default, when installing the Genero
Application Server) or as Domain Administrator (or a member of the Domain Administrators
group).
Back to the top
Authentication relies on Kerberos and it is assumed that the system
administrator has set up the participating servers to support Kerberos. The list
below summarizes the steps one must take to enable Kerberos authentication for a Genero application:
- Set authentication configuration in the Genero Application Server
configuration file (default as.xcf). See
Application Server Configuration Reference: Authentication for more
information.
- Configure the application to use authentication by adding an
AUTHENTICATION element to the application configuration. See
Defining Applications ,
Defining Web Services, and
Setting the Execution Environment for more
information.
- Update the Connector configuration file to use fully-qualified names for
the Genero Application Server hosts. See
Connector Configuration Reference for more information.
For a summarized walkthrough of implementing authentication for a GWC
application, see "Authentication for GWC Applications" in the Genero Web
Client Manual.
Back to the top
This section outlines the authentication process for an application requiring
authentication that is delivered via the Genero Web Client.
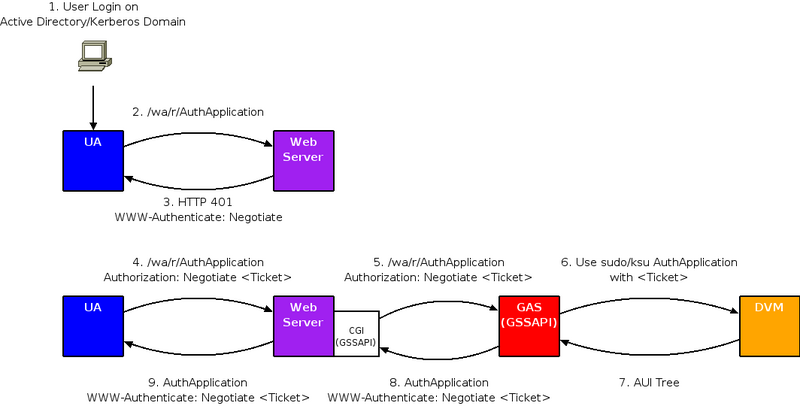
Authentication Process for a GWC Application
- User logs on to the domain (such as Active Directory).
- User attempts to access an application from a User Agent (browser), where
access to the application is restricted and therefore requires authentication.
For example, the user enters the URL for the application, such as
http://server.fully.qualified.domain.name:6394/wa/r/AuthApplication.
- User Agent receives an HTTP 401 response from the Web Server asking for
authentication credentials. The response header includes: "WWW_Authenticate: Negotiate".
An HTTP 401 response code is used when access to a resource is protected and
the client did not provide valid authentication credentials.
- The User Agent sends its granted ticket to the Web Server. The response
header includes: "Authorization: Negotiate <Ticket>".
At this point, the user is authenticated on the Web Server.
The Web Server can now relay the request for the
application through the Connector to the Genero Application Server.
- The Web Server Connector sends the application request to the Genero
Application Server along with another ticket that authenticates the user to
the server. The
ticket grants the access to the Genero Application Server; no additional
login or password information is required.
- The Genero Application Server starts the requested application by
launching a Dynamic Virtual Machine (DVM) as the authenticated user.
Note: When not using authentication, the DVM is started as the user
who started the Genero Application Server.
- The DVM sends the AUI tree to the Genero Application Server.
- The Genero Application Server processes the AUI tree using the Genero
Web Client and sends the resulting html page to the Web Server Connector.
- The Connector forwards the page to the User Agent.
Back to the top
Assuming your network has been configured to support Kerberos authentication,
this section outlines the steps you must take to enable Kerberos authentication for your application.
Note that this section is not intended to provide you with all possible
configurations for Kerberos within the Genero Application Server, but instead highlights
configuration changes necessary to implement Kerberos authentication in order for
a
Web application to be delivered by the Genero Web Client.
Step One: Configure the Genero Application Server
Configure the Genero Application Server to handle authentication
using Kerberos by configuring the <AUTHENTICATION> element in the Genero Application
Server configuration file (as.xcf):
<AUTHENTICATION Type="KERBEROS">
<REALM></REALM>
<SERVICE_NAME>gassvc</SERVICE_NAME>
<KEYTAB>$(res.path.as)/etc/gwc.keytab</KEYTAB>
</AUTHENTICATION>
See also Authentication Configuration
Reference
Step Two: Configure the application
Modify the application configuration to include an <AUTHENTICATION>
element. As only Kerberos authentication is supported at this time, specify
KERBEROS as the authentication type:
<APPLICATION Parent="defaultgwc">
<EXECUTION>
<PATH>$(res.path.fgldir.demo)/Widgets</PATH>
<AUTHENTICATION>KERBEROS</AUTHENTICATION>
</EXECUTION>
</APPLICATION>
See also Application List Reference
Step Three: Configure the Connector
Update the GAS Connector configuration file (connector.xcf) and replace all server IP addresses with fully-qualified domain
names:
<REQUEST_LIST>
<DEFAULT>
<SERVER>myserver.mydomain.com:port</SERVER>
</DEFAULT>
<REQUEST_LIST>
See also Connector Configuration Reference
Step Four (for Windows systems only): Configure Kerberos Service Principal
Names
Two Kerberos Service Principal Names are used:
- An HTTP service name is used by the User Agent for access to the Web
Server.
- gassvc service name is used by the Connector to ask for access to the
Genero Application Server.
Back to the top

